Trouble shooting
1. I received only one file (.crt or cer) which contains MydomainName.com Certificate
Look at the path in the certificate properties. If your certificate is at the root, then you don’t have any intermediate certificate.
You must only import the .cer ou crt you received.
If the path contains others intermediates certificates, then they will be needed. You can export theses certificates included in yours and create a file by certificate.

You can export each certificate listed in the path and get one file per certificate.
Double click on the certificate you want to export. Then go to Details / Copy to file.

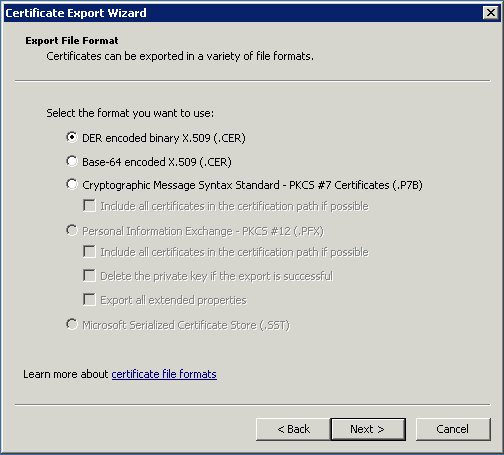
Click next. Default values are ok. Click next until you have to give a name. Confirm your exportation.
The result is a file .cer containing only the certificate exported. Repeat this exportation for each level of the path.
2. My private key is .pem. I cannot import my private key in Portecle
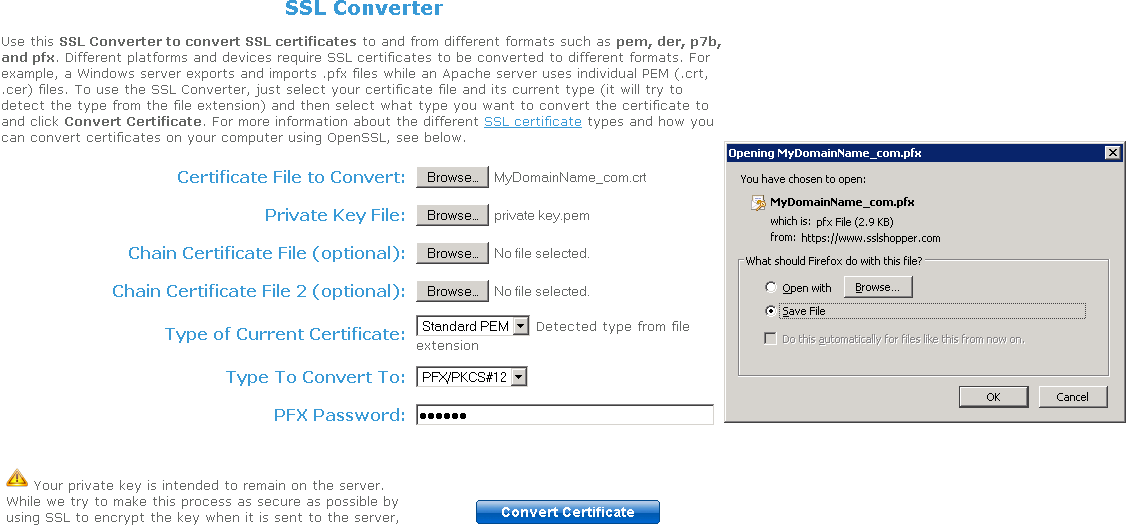
You can convert your .pem in pfx format with Tools or online sites. For example, on this site: https://www.sslshopper.com/ssl-converter.html
You must have your Private Key and your certificate (e.g. MyDomainName.com)
Browse to select the certificate to convert and the Private Key that goes with it. Current certificate type is PEM. Type to convert to is PFX (PKCS#12).
As .pfx is a secured format, you must enter a password. You can choose whatever you want, but, at least, you will have to set it to 'secret'.
So you should enter the password 'secret'.
The result is a .pfx format that you will be able to import in Portecle. As we saw in the installation section, this Private Key imported in Portecle must receive a CA Reply. See section Installation / CA reply for further information.
3. HTTPS errors
SSL error no cypher overlaps.

The Private Key or the Key Pair has not been imported in cert.jks or is invalid. Other errors types give the same screen with another error code.
Take a look at this code error. It concerns the certificate and something with it that goes wrong.
It is usually because one of the fields of the certificate is not valid or blank. Have a look to your certificate Properties and Request.
Verify that all the fields are correct. Report to section how to do a Request for more information.
4. Notice concerning Terminal Service Plus and Microsoft IIS web server
Please refer to our documentation about using IIS with Terminal Service Plus
However, here is some important information about IIS and certificates:
When using IIS, the certificate has to be installed in the keystore cert.jks. This must be done in the same way as if we were using Terminal Service Plus Web Server, and as described in the previous chapter.
Don't bind the 443 HTTPS port IN IIS, as this is the Terminal Service Plus Web server that handles the HTTPS protocol, the certificate and its encryption.
Not any bind has to be created on port 443. So, IIS must only have port 81 bound.
We are free to use IIS Request Tool to create the Private Key and the CA Request. It is simple to export the Private Key from IIS (IIS/Default site/Certificates) in the .pfx format and import it in cert.jks as described in the previous chapter.
Back to HTTPS, SSL & Certificates Tutorial Summary